
| Legal Information |
|

A good rule of thumb is that any computer connected directly to the Internet should also be protected by a firewall. A personal firewall can be your ticket to strong intruder protection and peace of mind.
If you are running Microsoft Windows XP Professional or Home Edition, Windows XP Media Centre Edition, or Windows XP Tablet PC Edition, you've already got access to a built-in basic firewall. Microsoft Internet Connection Firewall (ICF) is included as a Windows XP networking feature and you should enable it if you need firewall protection. If you've set up your Internet connection using the wizard and selected a direct or dial-up connection to the Internet, ICF may already be enabled.
You need protection if you have a direct, dial-up connection to the Internet, a single computer connected to a cable modem, or a single computer connected to a DSL modem. You'll also want to enable a firewall on the host computer (and only the host computer) that is used for Internet Connection Sharing (ICS).
If you're a broadband user with two or more ISP assigned IPs connected through a hub, you'll need to protect each computer individually.
When running Windows XP, ICF opens and closes most ports on the firewall dynamically as you access services but there are a few exceptions that require the manual configuring of ports to enable file transfer and voice calls.
Since Internet Connection Firewall provides inbound protection only, if you have concerns about programs that 'phone home' or send outbound data to an unknown destination over the Internet, you may want to consider a third-party firewall.
When it comes to architecture, you have two choices: a single firewall or a multilayer firewall approach (see Figures A and B).
 | 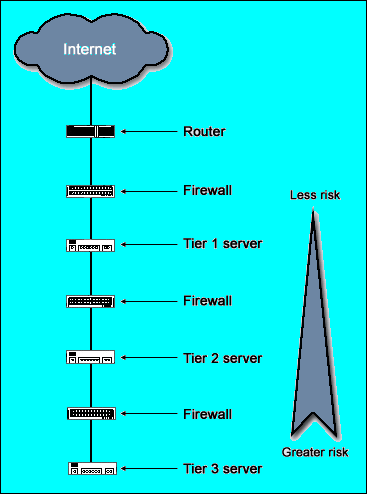 |
| Figure A Single architecture | Figure B Multilayer architecture |
To determine which would work best for your enterprise, you need to first understand expected computer use along with fleshing out and develop a security policy, because the two are tightly linked.
Application gateways and Packet filtering gateways are two types of firewalls available in the marketplace. Application gateways are causing some computational problems in computers due to heavy CPU usage, therefore on busy networks Packet filtering devices are more preferable.
However, the vendors are trying to embed these two inevitable characteristics of firewall into one.
Installing a firewall into a gateway is not a security panacea. Security vulnerabilities are discovered every year with just about every firewall in the market. However, the worst thing might be the misconfigured, unattended and unmaintained ones.
There are many tools out there to test the security of our applications. Some methodologies are needed to intrude into systems in our tests. We need to understand the ACLs (access control lists) of a firewall or a router, we need to map what is behind the firewall, we want to know what is allowed in and so on.
Finally, take into account the financial considerations of a firewall technology purchase -- you don't want to buy too much or unneeded protection, but you will have to provide for ongoing maintenance costs.
While a security policy and firewall plan should be created and developed, that's not where security ends. IT administrators must ensure they have all vendor patches properly applied and that each system is kept up-to-date.
The true value of a firewall system is in the constant maintenance of all resources.
Comprehensive security requires safeguards in a layered defensive approach. Keep in mind that your ultimate solution must be flexible enough to provide for scalability and growth.
| Search Knowledge Base | Feedback |