
| Legal Information |
|

Most concerning is the increasing trend of malicious spam. Customers of almost every major international bank have been targeted by phishing scams of varying sophistication. Phishing is the term given to a specific type of spam that attempts to fool people into supplying confidential information -- the spammers are effectively "fishing" for whatever information they can find.
Essentially, phishing involves an attacker attempting to gain the trust of a victim and fool them into taking certain actions.
The normal format of a phishing scam is an e-mail that looks official (impersonating the official site), is apparently sent from the bank itself, and that requests you to input your personal details (often including credit card and PIN number) for the purposes of account confirmation. These e-mails generally use genuine logos and text styles, often taken directly from the bank's Web site, to try to fool the recipient.
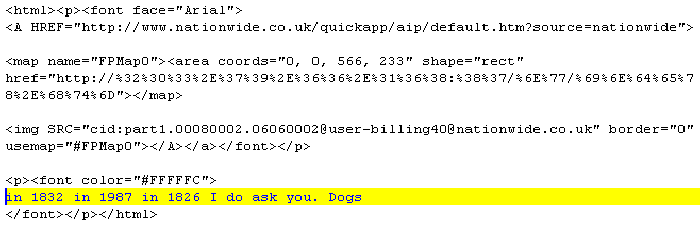
The above shows some HTML code split into blocks for easy reference. Let's go over it step by step:
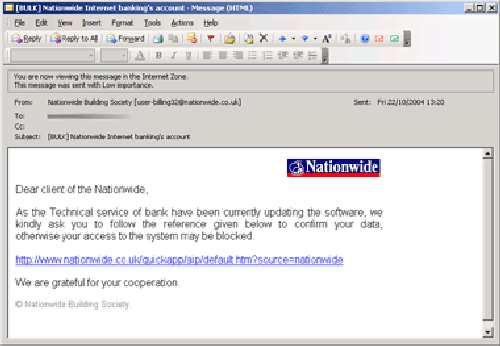
If you were unlucky enough to accidentally open spam e-mail, you may have noticed it was quickly followed by more spam. It's no coincidence -- spammers use clever tracking mechanisms to monitor whether their e-mail is deleted, opened, or even forwarded to another person.
The most obvious and basic tracking mechanism is a read receipt . A read receipt is a flag in the e-mail header that tells your e-mail client to return the status of the e-mail to its sender. Through this system, the spammer can obtain basic information about whether you read or deleted the e-mail. Every popular e-mail client (such as Outlook or The Bat) has an option to deny read receipts for public e-mail received from the Internet. If you use a corporate e-mail system, such as Microsoft Exchange, the system administrator usually has the ability to force your e-mail client to return read receipts so beware!
A more sophisticated tracking system is achieved through web bugs. Adware systems can track your Web browsing and application usage habits. The same principle applies to e-mail. Using HTML e-mail, a spammer can include a reference to a script on its server that's executed every time the e-mail is opened and the content is loaded.
To achieve this, a single pixel, transparent GIF image is included in the e-mail. This GIF is invisible to the reader, but essential to the tracking system. When your e-mail client loads the image, the tracking script on the spammer's server is executed, completing the vicious cycle.
This is the reason you should never open an e-mail you have good reason to believe is spam.
If you forward an e-mail with a Web bug in it, the spammer will know exactly who you forwarded it to and retrieve personal information on them. E-mail client security vulnerabilities are an absolute goldmine for spammers, the chief culprit being IFRAMEs.
| Search Knowledge Base | Feedback |