
| Legal Information |
|

More and more botnets and Trojans with two-factor authentication using session riding are occurring, but it can also be done with hijacking via cross-site scripting. Session riding is an analogy.
If I am a spy and I need to get into a military base, I am going to put myself under someone's truck and hold on to the truck while they go through the military security and the military security opens the gates and lets in the truck. I am still under the truck, no one knows I am under the truck, and once he is in, I get out from under the truck and I have now infiltrated the military base. This is the same thing. All I am doing is riding against the session that another user is taking. He does not know I am there. I am going to get his session cookies and get a host to his system.
In cases like this, you do not need a spoof phishing site.
The figure below is an example of using the real site to cause real damage. This is truly an Amazon site. We sent out an e-mail to a user with a true Amazon link. We said, you need to change your settings at the time you change your password. We ask them to login.
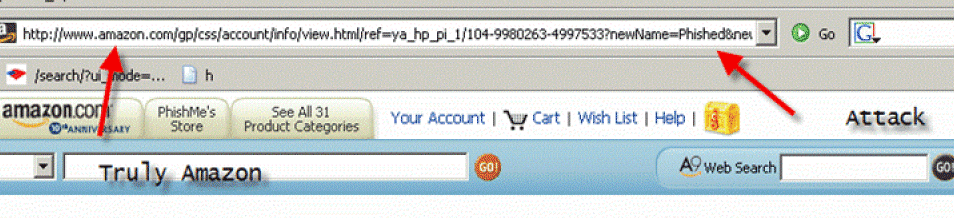
If they log in, we do not know they are logging in yet. But once they log in, we found a setting that allows us to change the name of the site.
At this part it says, 'You have successfully modified your account.' If you look at the tab near where it says Your Account, it says PhishMe's Store. In the second frame the tab is now says Phished's Store. The user name and the password have been changed. The user helped do that because they were set on a poisonous link that exists on Amazon and session rode them, logging in and then changing and resetting their password and sending it me. So this is an example of a good session riding.
Another trick is to mess with Amazon wish lists. And the reason why this was possible is because Amazon had 90-day session cookies. Every time you go to Amazon, if you do not specifically log out or indicate that this is not me, it is going to recognise you for over 90 days. If you go to some other site, it will add the book secretly to the wish list by making a get request or an image source request if they add the book.
With request forging. An attacker can make a request through a trusted site like www.amazon.com. He can control the victim's responses and use him to attack other sites or attack that site. In this diagram, we are going through the target site.
The victim clicks on it and now he has control of the victim's browsing experience interactively.
| Search Knowledge Base | Feedback |