
| Legal Information |
|

How do you know if you're already a victim? In most cases, the results are obvious:
Some spyware is not so obvious and easy to spot. On the whole, your operating system and Web browser may appear to work correctly, but random advertisements appear as you browse and Web sites you used to be able to get to are no longer accessible.
Some spyware is downright sneaky and may give absolutely no indication at all that it's installed. Your only clue may be that your computer is running a little slower than it used to, and files don't download quite as fast. It's time to locate the culprit.
The moment your computer starts doing something funny, it's very easy to immediately conclude that spyware must be the cause. In reality, most people have fairly fixed Web browsing habits and visit the same small set of Web sites repeatedly, only visiting new Web sites when prompted to by links or e-mails. In this scenario, it's relatively rare to become a spyware victim, especially if the Web sites browsed are respectable ones.
Quite often, a slow computer can be because of failing hardware, a fragmented hard disk, or a new utility program. If you think your computer has been infected by spyware, follow the investigative steps but don't rule out other causes straight away.
The easiest way to locate hidden spyware is to investigate the mechanisms spyware uses to hide and do its work. A lot of spyware communicates back to its creators via the Internet. An easy way to verify communication is occurring is to view all of the current, active network connections on your computer using Active Ports.
Active Ports is an essential tool that lists all incoming and outgoing connections for all the active network connections, such as your Internet dial-up or broadband connection.
The Active Ports window shown below is split into a number of columns, the most important of which are:
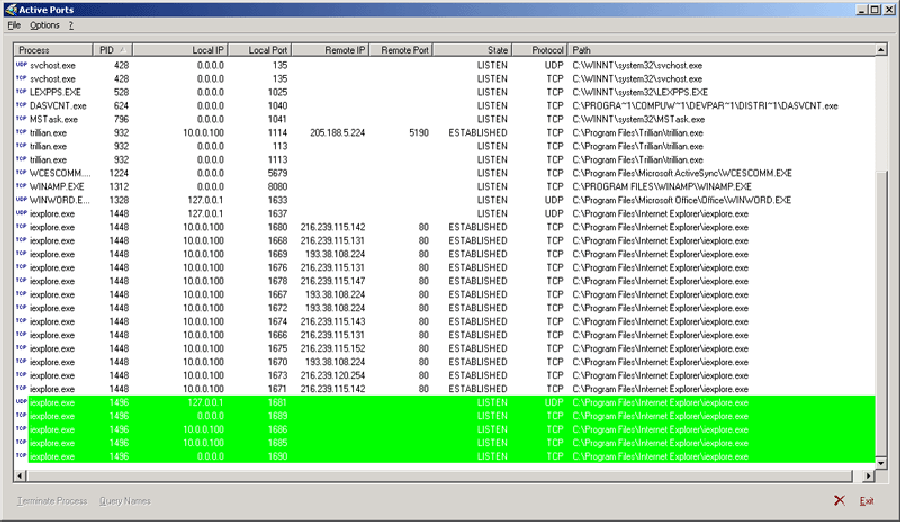
Using the output from Active Ports, it's easy to see whether any rogue processes are making network connections. Even more useful is the ability to watch for new connections being made. As an example, open Microsoft Internet Explorer and wait until your home page loads (if your home page is a blank page, browse to a Web site you normally use).
Quickly switch back to Active Ports, and you'll see a new entry in the window highlighted in green similar to the above figure.
The process name is iexplore.exe, and the IP address of the Web server that hosts your home page also appears in the list. After the page has loaded, a few seconds pass and the Active Ports entries that were highlighted in green turn red. This signifies that the connection is now closing.
Active Ports highlights new connections in bright green, and terminating connections in bright red.
If spyware is present on your computer and is communicating to a remote server, you'd spot it in this list. The best method for investigating this is to close all applications, open one Internet Explorer window, and then watch the Active Ports output for a while. If spyware is communicating with a remote server, it usually gives itself away here.
WARNINGIf you use Norton Antivirus, you may find that Active Ports (and other similar, legitimate tools) are detected as spyware. This is actually a false-positive, and can be safely ignored. These tools are not spyware and do not contain malicious code.
Alternatives to Active PortsYou may find the following tools helpful alternatives to Active Ports ( Active Ports doesn't work with Windows ME):
Microsoft Windows itself will quite often seem to make network connections at random. The only way to separate these legitimate connections from malicious, spyware connections is through experience.
Another favorite spyware trick is to fill up your hosts file with invalid entries for valid Web sites. When you type a URL (Uniform Resource Locator) into your Web browser, such as http://www.cnet.com, the Windows network stack uses various methods to resolve the FQDN (Fully Qualified Domain Name, for example www.cnet.com) into an IP address.
The first method Windows uses is to interrogate the hosts' file. This is a plain-text file, shown below, stored deep within the Windows directory structure that contains a list of FQDNs and the IP addresses to which they resolve.
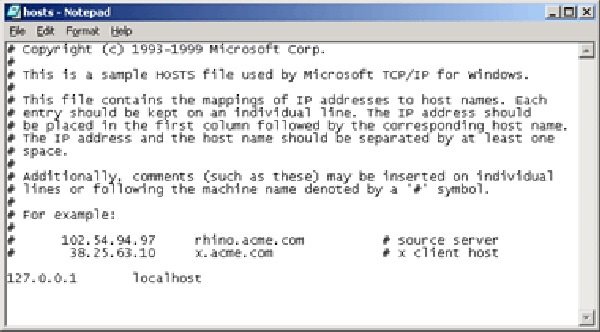
If spyware adds the FQDN of a Web site to your hosts file along with an incorrect IP address, you cannot access that Web site. This could be a real problem if the Web site in question is www.download.com, and you need to download a spyware removal tool.
Under normal circumstances, a hosts' file has one 127.0.0.1 entry as in the above figure . If yours has a lot of entries for Web sites, something suspicious may be going on.
If spyware is running, it will invariably show up as a process on your computer. Fortunately, the filenames and Registry keys used by all but the newest spyware are well known -- thanks to the efforts of antispyware researchers. A quick way to determine whether any spyware processes are running is to view the current task list through Windows Task Manager, as in the figure below.
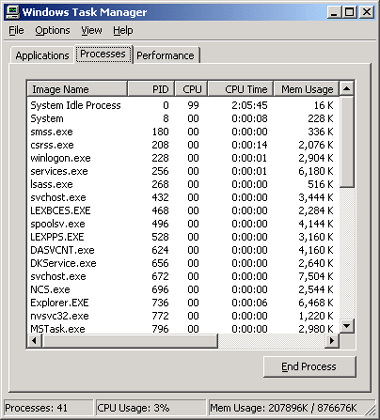
As mentioned previously, the only sure-fire way to know if a rogue process is on your system is to gain experience in which processes are harmless and common. If you do spot a suspicious process, make a note of the process name and use the End Task button to kill it.
Next, use the Windows Search function to locate the file on your hard drive. Don't delete it immediately though -- it may be an innocent system file!
It can be very difficult to decide whether an executable is a legitimate system or application file, or malicious spyware. Sometimes the directory it resides in is a good indication, but many spyware programmers deliberately write their files to the Windows system directory and name them as close to legitimate system filenames as possible. Before deleting any files you should always search the Web for the filename in question -- the results are usually conclusive and help with diagnosis.
Also visit the WinTasks Process Library to see which processes are specific to Windows.
| Search Knowledge Base | Feedback |