Good Knowledge Is Good2Use

HijackThis is an interesting anti-spyware tool in that instead of attempting to detect rogue applications as Spybot does, it targets the methods used by spyware to infect a computer. This means that it will find and list absolutely every program using these methods, regardless of legitimacy.
Spyware often uses the same features and flaws that legitimate applications use to provide their functionality. This makes HijackThis an extremely powerful tool, but one that can easily cause irreparable damage.
It can be downloaded here.
WARNING
To reiterate an absolutely critical point, HijackThis locates and allows you to delete absolutely anything it believes is using a feature that spyware may use. Items listed by HijackThis are very often not spyware! Do not, under any circumstances, use it to fix or remove any items you're not absolutely sure about.
HijackThis is distributed as a single executable inside a Zip file. To run the tool, just extract HijackThis.exe from the Zip and run it as normal. Although the user interface isn't as intuitive as some applications, it's fairly easy to get to grips with. Click Scan to generate a report similar to the one in below.
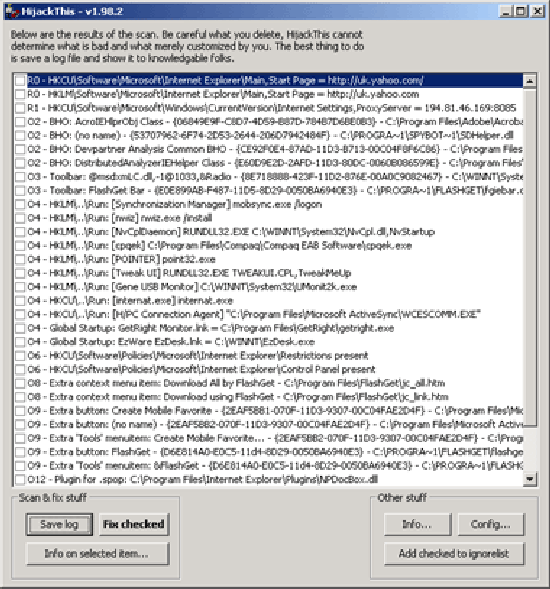
HijackThis scan report.
It's not as user friendly as Spybot, but the information is invaluable. The HijackThis window should look similar to that shown below although you may not have as many items listed. You'll notice that each item has a letter and number preceding it. Each of these codes has a different meaning; if you click Info, a window opens that explains the meaning of each code.
Interpreting the scan results is a complex task. Here are some of the common item codes, and what they mean:
- R0: Default browser Web pages. If Internet Explorer is loading the wrong page for the home page or search page, these are the items to check. If a proxy server has been configured, it will be listed here too.
- O1: If a bad page appears whenever you mistype a Web site address, this item tells you whether your hosts' file has been hijacked.
- O2: A list of all the BHOs installed on your system. You should check all O2 items very carefully each time you run HijackThis to ensure you know exactly which applications have registered BHOs. In the above you can see Adobe Acrobat, Spybot, and Compuware Devpartner are listed, which are all legitimate applications.
- O3: A list of all the Internet Explorer registered toolbars. If you have a toolbar you didn't install, it shows up in this list.
- O4: A list of all the executables that start when Windows boots and when you log in. Many legitimate applications use cryptic filenames, so be sure to search the Web to check what each executable is before deleting anything.
- O5, O6, and O7: these codes relate to the use of Windows policies to force certain behaviours, for example to disable the Internet Options applet in Control Panel. If you find that you can't access certain configuration options, these are the codes to check.
- O13: If you can access Web sites correctly when prefixing the site address with http:// but omitting that prefix causes a bad page to load, this is the code to look for.
- O18: These items are all the protocols and filters installed on your computer. Some spyware integrates itself using a filter so that it can capture and analyse every Web page you visit. If any items appear under O18, be sure to investigate them.
HijackThis has a fairly comprehensive explanation system for all of its codes. To access it, click Info . Locate the code you want to learn more about and highlight the entire line of text. Click Info on selected item , and a message box appears with some further details. The information message box for BHOs is shown in below.
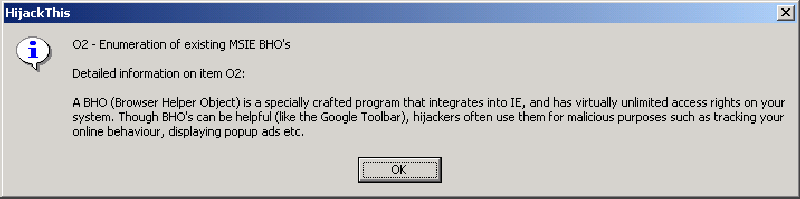
Further info on BHOs.
© Copyright 1998-1999 GOOD2USE



