
| Legal Information |
|

One sophisticated way of generating SPAM is to secrete software robots or bots on a number of PCs. This then constitutes a network of bots or a botnet. The bots being programmed to send emails without their users realising it.
While the term "botnet" can be used to refer to any group of bots, such as IRC bots, the word is generally used to refer to a collection of compromised machines running programs, usually referred to as worms, Trojan horses, or backdoors, under a common command and control infrastructure.
A botnet's originator (aka "bot herder") can control the group remotely, usually through a means such as IRC, and usually for nefarious purposes. Individual programs manifest as IRC "bots". Often the command and control takes place via an IRC server or a specific channel on a public IRC network. A bot typically runs hidden, and complies with the RFC 1459 (IRC) standard.
Generally, the perpetrator of the botnet has compromised a series of systems using various tools (exploits, buffer overflows, as well as others; see also RPC). Newer bots can automatically scan their environment and propagate themselves using vulnerabilities and weak passwords. Generally, the more vulnerabilities a bot can scan and propagate through, the more valuable it becomes to a botnet controller community.
Botnets have become a significant part of the Internet, albeit increasingly hidden. Due to most conventional IRC networks taking measures and blocking access to previously-hosted botnets, controllers must now find their own servers. Often, a botnet will include a variety of connections, ranging from dial-up, ADSL and cable, and a variety of network types, including educational, corporate, government and even military networks.
Sometimes, a controller will hide an IRC server installation on an educational or corporate site, where high-speed connections can support a large number of other bots.
Exploitation of this method of using a bot to host other bots has proliferated only recently, as most script kiddies do not have the knowledge to take advantage of it.
Botnet servers will often liase with other botnet servers, such that a group may contain 20 or more individual cracked high-speed connected machines as servers, linked together for purposes of greater redundancy. Actual botnet communities usually consist of one or several controllers who consider themselves as having legitimate access to a group of bots.
Such controllers rarely have highly-developed command hierarchies between themselves; they rely on individual friend-to-friend relationships. Often conflicts will occur between the controllers as to who gets the individual rights to which machines, and what sorts of actions they may or may not permit.
This example illustrates how a botnet is created and used to send email spam.
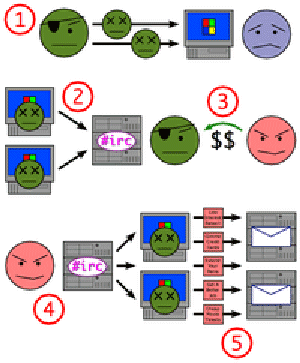 |
|
Botnets are exploited for various purposes, including denial-of-service attacks, creation or misuse of SMTP mail relays for spam (see Spambot), click fraud, and the theft of application serial numbers, login IDs, and financial information such as credit card numbers.
The botnet controller community features a constant and continuous struggle over who has the most bots, the highest overall bandwidth, and the largest amount of "high-quality" infected machines, like university, corporate, and even government machines.
Botnet Lifecycle| Search Knowledge Base | Feedback |