
| Legal Information |
|

Strong and consistent security services are essential to corporate networks. Managing user authentication and access control is often tedious and prone to error. Active Directory centralises management and enforces role-based security consistent with an organisation's business processes. For example, support for multiple authentication protocols such as Kerberos, X.509 certificates, and smart cards combined with a flexible access control model enables powerful and consistent security services for internal desktop users, remote dial-up users, and external e-commerce customers. The following are some ways in which Active Directory strengthens security:
One of the most important architectural advantages of Windows 2000 Server is the integration of Active Directory and its advanced security features that enable a new level of data protection. This is particularly important for organisations that do business over the Internet.
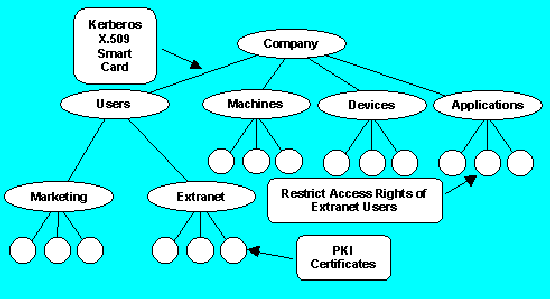
In addition, Active Directory natively supports a fully integrated public key infrastructure and Internet secure protocols, such as LDAP over SSL, to let organisations securely extend selected directory information beyond their firewall to extranet users and e-commerce customers. In this way, Active Directory strengthens security and speeds deployment of e-business by letting administrators use the same tools and processes to manage access control and user privileges across internal desktop users, remote dial-up users, and external e-commerce customers.
| Search Knowledge Base | Feedback |