
| Legal Information |
|

ISA Management. Internet access can be done with access policy. Here we configure all of the policies. There is a single Management Interface, a manageable and scaleable snap-in. With one snap-in, you see all of the areas on the single enterprise. Administrators benefit from a single management interface for firewall and Web caching. Here we talk about outgoing access policy. After you install ISA the first time, then you have to configure access policy for your internal clients to go out. By default, ISA does not allow anybody to go out or allow any protocols to go out. You have to configure the access policy the first time.
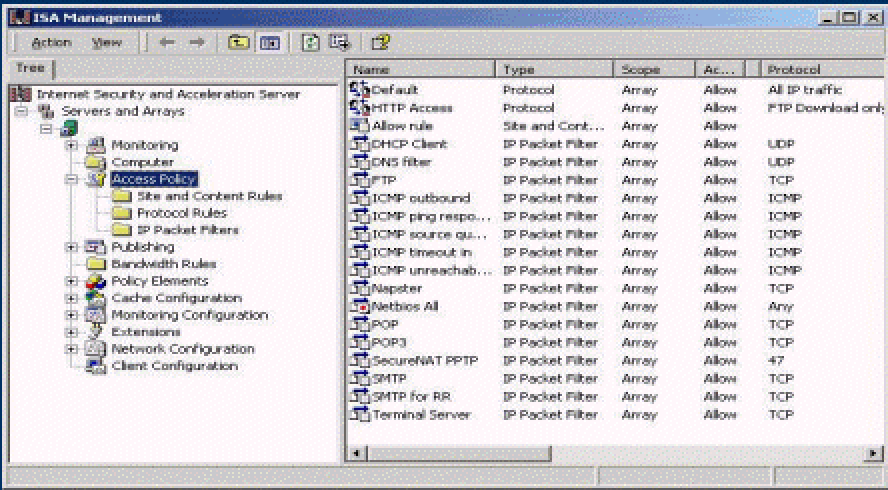
You can use the ISA Server to configure site and content rules, and protocol rules that control how the internal clients access the Internet, but this is the first thing you need to do to allow internal clients to go out to the Internet.
Site and content rules specify which sites and content can be accessed. Most of the time, what you do is allow all of the rules first, and then you start denying so that you know ISA can allow all of the clients who are trying to access the Internet via access policy. You open the ISA the first time and then start denying. Protocol rules indicate whether a particular protocol is accessible for inbound and outbound communication.
The ISA Server, ISA 2000, does have a lot of help files. If you click on the help files and search for access policy, you will find a lot of good documentation on exactly how to configure access policy.
Under access policy you create IP packet filters, protocol rules, and site and content rules. This way you just allow all of the rules so that your internal clients can go out in the beginning without any protection. Then you start denying protocols or filter the packets. So a great way to start out with ISA is using help.
At some point you may wish to make access or more restricted - hardening. Go to the security template for Windows 2000 first. That's a snap-in.
Policy access rules work the same way with each of the three client configurations The differences are with the clients.
If it's a Web Proxy client or a firewall client, the rule will function the same way, it will just change whom it's applied to based on the Windows user name or user group. If it's a SecureNAT client, then it will apply to them based on IP address, but the actual function of the rule, of the policy, will be the same.
| Search Knowledge Base | Feedback |