
| Legal Information |
|

To connect the two locations together you have a couple of options:
You will need two VPN-capable routers (and know how to create a 'normal' tunnel between them) and two public IPs on the site where ISA is located.
Your setup should look like this:
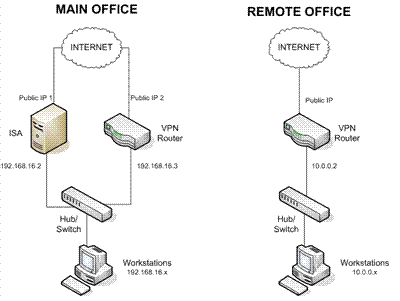
Basically, what you need is to give ISA and the VPN router in the main office 2 distinct public IPs and put them parallel to each other. Then turn off the DHCP on the VPN router on the main office and make sure is on the same subnet as the internal LAN and connect it to the same switch as the SBS internal NIC.
Configure the VPN link between the 2 sites as you would in a "normal" situation and make sure your VPN router is blocking all incoming traffic. As with any VPN the remote LAN must be on a different subnet.
Now, the last step would be to tell the local LAN how to find the remote one (since SBS is the default gateway the computers will try to use that one instead of the VPN router). To correct this we must create a static route on the server. Run the following command on the SBS box
route add -p 10.0.0.0 mask 255.255.255.0 192.168.16.3and you should be good to go.
There could be other variations in this scheme, but if you understand the steps involved here then its easy to modify this to do whatever you want.
One criticism of this solution is that it can be seen as a violation of one of the cardinal rules of firewalling, that you should never permit alternative paths into the corporate LAN.
This and other alternate entrypoints. like unsecured or improperly secured WAPs, travelling/guest laptops which connect directly into the network are variations on the "infection by floppy" problems of the 1980's. It's very costly to implement safeguards if you believe in the traditional "trusted zone" firewall principle but make a mistake allowing an exploit through in some way and VPNs can be a highway into the LAN.
However, this solution, like any other solution, depends on how you configure it. In the routers you need to be able to block all inbound and outbound traffic (except for the VPN) and control the remote and main LANs. The greatest concern is for the VPN per se.
A much better (secure) approach would be to put the VPN endpoint in front of ISA and publish the necessary ports (i.e. Terminal Services) and don't forward them on the router. This way the VPN tunnel only has access to what they need instead of the whole lan.
| Search Knowledge Base | Feedback |