
| Legal Information |
|

The Risk Assessment will be conducted by reviewing the functions of the Infrastructure, and then considering the types of events that might occur in both normal and unusual situations. This may be done by challenging the normal assumptions and considering the possibilities of unanticipated situations. For each risk event, the underlying (root) cause should bedetermined that will create the potential risk occurrence.
Risks are ranked by scoring various criteria with appropriate numerical ratings, adding the scores to determine the overall score of each risk, and sorting the risks into descending order based on each score. A risk scoring threshold is established, over which risks must be reduced using adequate design and/or process controls that will protect the system. Those risks that fall below the threshold are either unmitigated or scheduled for later action.
An additional threshold or characteristic of risk can be used to determine the differentiation of non-mitigation versus postponed mitigation.
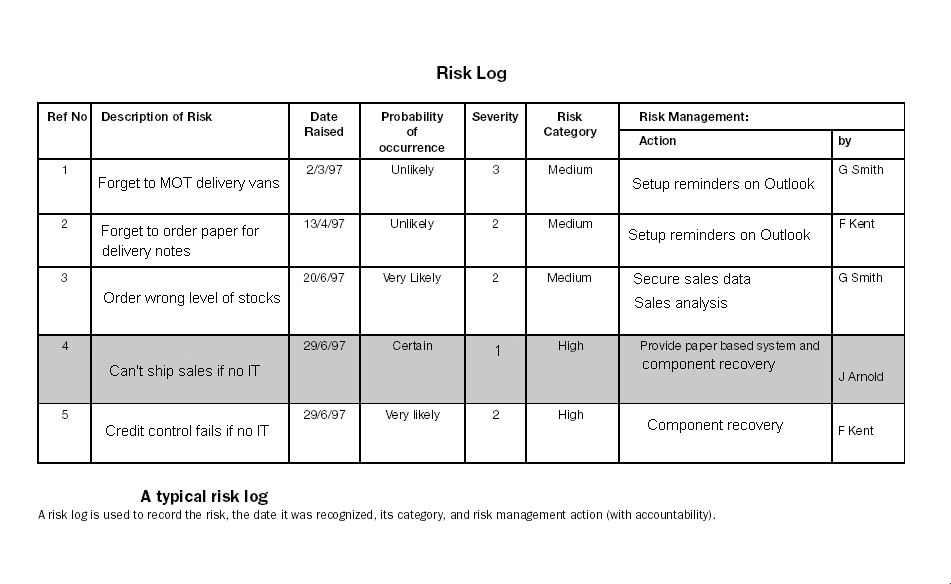
For each identified risk event, the means of reducing risk (system design or operational features) including manual tasks defined in the system operating procedures, are described in the risk assessment documentation.
Risks with rating scores that meet or exceed the Risk Threshold will require reduction by adding additional technical enhancements or procedural controls to the system.
In order to organise the output from the risk assessment exercise, the following guidelines should be followed
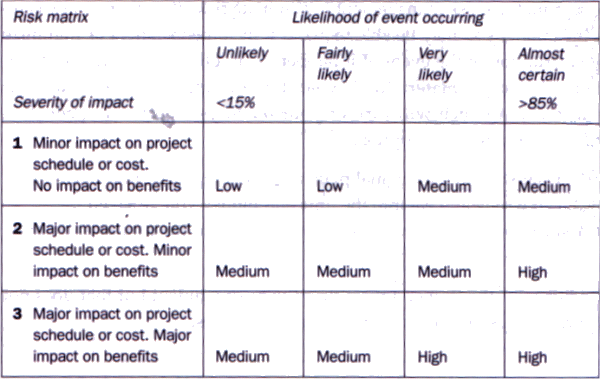
This ranking indicates the criticality of the event by its impact on the operation of the system. The highest rating is given to a risk that the system might fail if the event occurs, either through the inability of the system to continue, or corruption of the accumulated data occurring. A lower ranking will be used for impacts that do not stop the system, nor corrupt data, and can be offset via other mechanisms, including manual workarounds.
This ranking indicates the probability that the event will actually occur sometime during the system's life. The highest ranking goes to the event that can be expected to occur at some point, with lower rankings to those events that only might occur, or are not expected to occur at all.
If the risk event is detected, via other system or manual activities, prior to the time that the risk event causes an impact, that detection likelihood reduces the risk. The highest ranking goes to events that are not likely to be detected, and lower rankings are used for possible or expected degrees of detection of the event.
| Search Knowledge Base | Feedback |