| Legal Information |
PC Knowledge Base - Firewall Testing: Test The Firewall Functions In Your Test Environment
|
Good Knowledge Is Good2Use

Establish a test configuration so that your firewall system is interconnected between two isolated hosts, one playing the role of the external world and the other playing the role of your internal hosts.
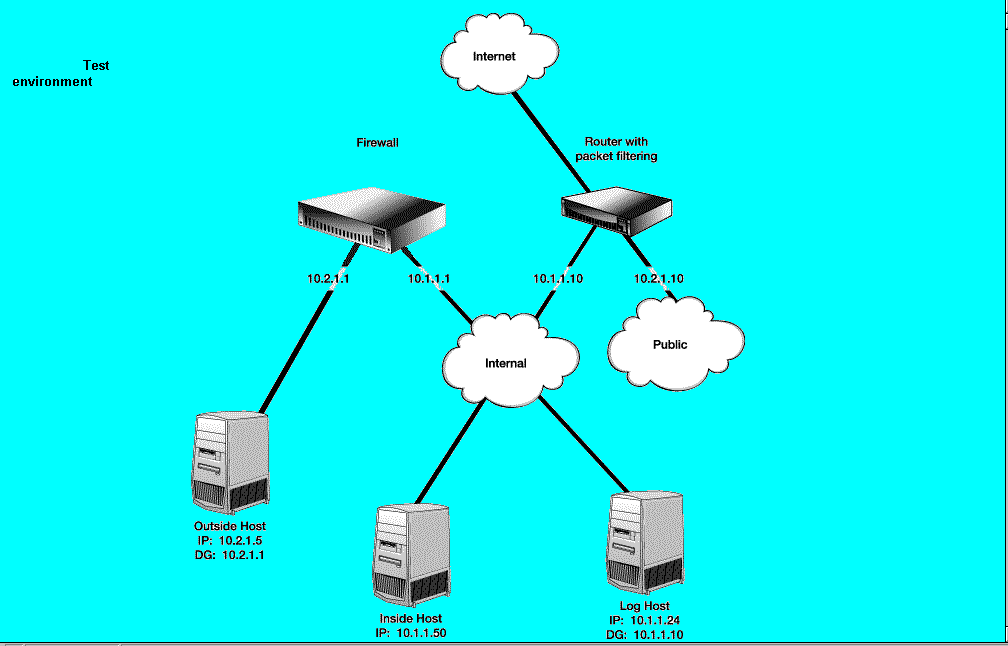
Ensure that the default gateway for the internal host is set to the firewall system under test. If you have chosen an architecture that supports centralised logging (recommended), place both the internal host and a log host on your internal network so that you can test logging options. If logging is performed on the firewall host, you can connect the internal host directly to the firewall host.
Have scanning or network sniffing tools in place on your outside and inside hosts to capture all traffic in both directions (inside to outside, outside to inside).
Perform the following steps:
- Disable packet filtering.
- Inject packets that will exercise all routing rules and send these through the firewall system.
- Ensure that packets are routed correctly by examining the firewall logs and your scanner results.
- Turn on packet filtering.
- Inject network traffic that is an appropriate sampling of all possible source and destination IP addresses, across all ports, and for all protocols.
- Ensure that packets intended to be blocked (denied) are blocked. For example, if all UDP packets are to be blocked, ensure that none get through. Ensure that packets intended to enter or exit (permitted) do enter and exit. Do this by examining your firewall logs and scanner results.
- Scan for open and blocked ports to ensure your firewall system is performing as intended.
- Examine all of the network traffic that is logged and verify that the logging options associated with each packet filtering rule are operating as intended.
- Examine all of the network traffic that is logged and verify that the alert options associated with each logging option are sending alerts to the designated destination (such as the firewall administrator) using the specified mechanism (such as paging or email).
Plan to conduct this step and testing in a production environment with at least two people. One being: the original implementer of the routing configuration, packet filtering rules, logging options, and alert options, and an independent person who reviews what has been implemented, understands the intent, and agrees that the network topology and security policy have been reflected correctly.
© Copyright 1998-1999 GOOD2USE


