| Legal Information |
PC Knowledge Base - Firewall Testing: Test The Firewall Functions In Your Production Environment.
|
Good Knowledge Is Good2Use

This step assumes that you are migrating from a single layer firewall architecture (see figure "Single layer firewall architecture") to a multiple layer architecture (see figure "Multiple layer firewall architecture").
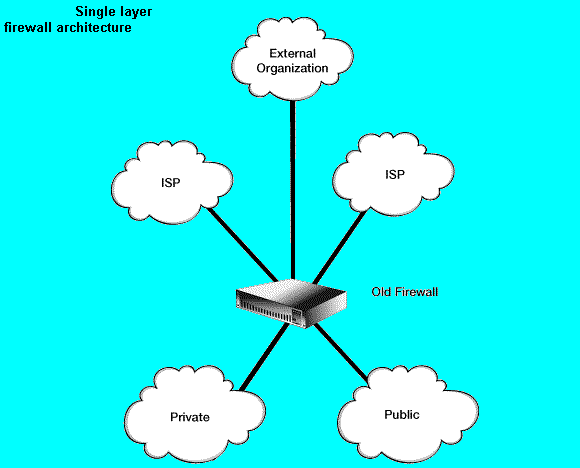
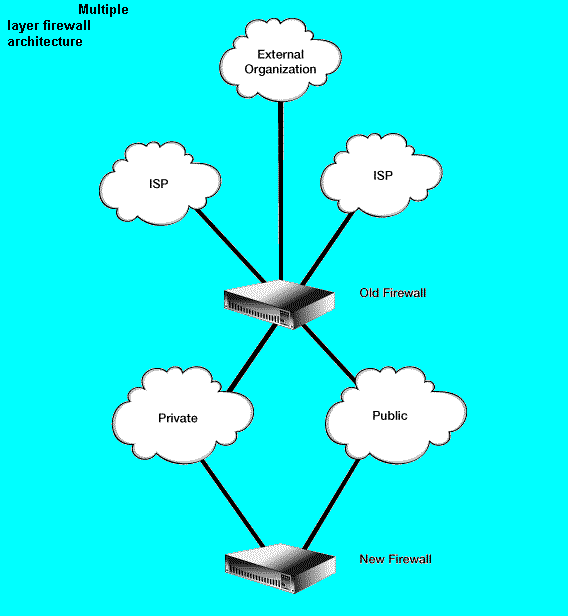
This step also assumes that you have a network topology of one or more private networks and one or more public networks. The public networks typically connect hosts that respond to internal and external requests for service such as WWW (HTTP), FTP, email (SMTP), and DNS.
These hosts may also respond to internal requests for service such as SNMP, file access, and logging. The public network as described here can serve as your DMZ. The private network typically connects hosts that service your internal users including individual user workstations.
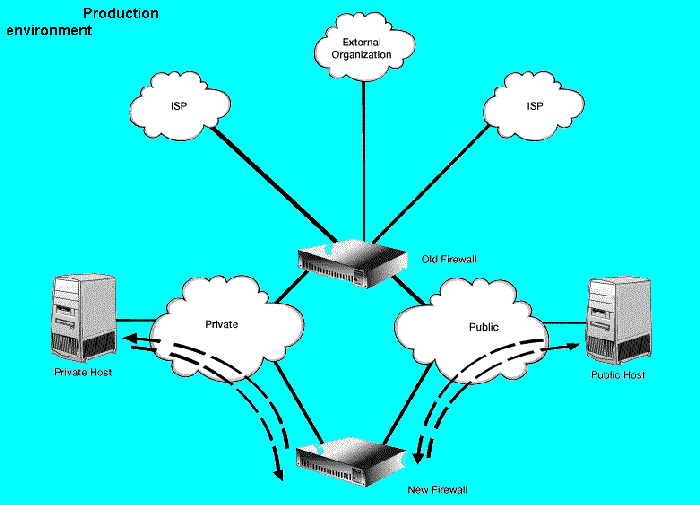
Perform the following steps:
- Connect your firewall system to your public and private networks.
- Set the routing configuration on selected public and private network hosts to direct traffic through the firewall system.
The basis for selection is on a service-by-service basis, for example, the Web server on your public network and the host storing the files that the Web server needs to access on your private network. Cycle through the selection and exercise of all services such as Web, file access, DNS, mail, and logging. See figure "Production Environment".
- Log the firewall system's incoming and outgoing network traffic. Use a scanner or network sniffer to observe what is happening.
- Ensure that packets intended to be blocked (denied) are blocked. For example, if all UDP packets are to be blocked, ensure that none get through. Ensure that packets intended to enter or exit (permitted) do enter and exit. Do this by examining your firewall logs and scanner results.
- Scan all hosts in a selected portion of your network that includes the firewall system. Verify that you cannot gain any undesired information due to the scanning packets being blocked (denied). Attempt source port scanning using a well-known port such as the FTP-data port (port 20) to ensure that you cannot use the port for a service other than the one intended.
- You can use intrusion detection system tools in a simulated network traffic or live network traffic test to aid you in determining if your packet filtering rules are protecting your systems and networks from known attacks. You will need to run these tools for some period of time and review the results on a regular basis. You may want to defer this level of testing to normal operations once you have fully deployed the new firewall system.
- Examine all of the network traffic that is logged and verify that the logging options associated with each packet filtering rule are operating as intended.
- Examine all of the network traffic that is logged and verify that the alert options associated with each logging option are sending alerts to the designated destination (such as the firewall administrator) using the specified mechanism (such as paging or email).
You cannot do a final test of your routing configuration prior to connecting the firewall system to your operational external interfaces (refer to ô9.
Install the firewall system.ö and ô10. Phase the firewall system into operation.ö). As a result, you should run live packets through your internal networks using the new firewall system to the greatest extent possible prior to connecting to the outside world.
To mitigate the risk of unexpected problems in this final test phase, you should initiate the operational connections for a small subset of hosts (such as those used by your system and firewall administrators) prior to connecting large numbers of user workstation or server hosts.
© Copyright 1998-1999 GOOD2USE




