
| Legal Information |
|

One of the main aims of firewall testing is to try not to trigger intrusion detection software, in testing failures give rise to opportunities for improvement. Consequently, we don't want to deploy full connection (3-way handshake) port scanning. Port scanners trigger these systems easily because of the enormous amount of SYN/ACK packets sent back and forth to every port of the firewall just to check them. Therefore, we don't like this noisy stuff in our tests.
Moreover, we should know that, most of the firewalls do not respond to ICMP echo requests (ping), as long as it is configured by an expert firewall administrator.
Traceroute is a network debugging utility that attempts to map all the hosts on a route to a certain destination host/machine. It sends UDP datagrams by default or ICMP ECHO Request packets with TTL (time to live) fields set to 1 just before reaching the final target.
Once the target reached, as TTL field gets zero, the target will discard the datagram and generate an ICMP Time Exceeded packet back to its originator. It is worth noting that Windows systems use ICMP ECHO Request by default and you can not use UDP method with Microsoft's traceroute implementation, "tracert".
Lets assume that a network is protected by a access control device, a firewall or some sort, and it denies everything in but dns traffic. A regular traceroute will be as follows:
 |
As you see from the preceding example, we can not go beyond 10.10.0.6 which most probably means that there is a blocking device at hop 4. To understand this we have to dig a little deeper.
When traceroute is deployed with default UDP datagram option, it will increase the port number at every time it send a UDP datagram. Hence, we need a equation which will give the starting port number to reach to final target. So the starting port number is
(Target port - (number of hops * number of probes)) -1where
number of hops is from our probing box to the firewall, andKnowing this, know lets look at our tracerouting
number of probes is by default 3.
 |
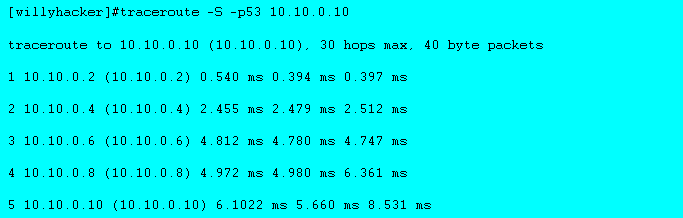
BOOM !, we penetrated in to firewall, which is 10.10.0.8 and get into the network which is most probably a DMZ. However we could not get a reply from 10.10.0.10. The reason is basic, we did not hit to UDP port 53 of this box. As traceroute has incremented our port number again and it has got stuck to ACL on the firewall.
Don't worry, Mike Shiffman (the author of famous firewalk), has a remedy for that. With his modified version of traceroute, traceroute 1.4a5 you can grab it
from (www.packetfactory.net)
 |
As a result, to test other open ports we can try other ports, with a home grown script, it can be done systematically.
| Search Knowledge Base | Feedback |